Symantec End-user Endpoint Security Review

Our score 8.7
What is Symantec End-user Endpoint Security?
Impressive and Effective Endpoint Security Software
I recently had the opportunity to test out a powerful and comprehensive endpoint security software that completely exceeded my expectations. This software provided top-notch protection for my devices and ensured that my sensitive information remained secure at all times.
Pros:
- Easy to use interface
- Real-time protection against threats
- Robust endpoint security features
- Regular updates to stay ahead of new threats
Cons:
- Can be a bit resource-intensive on older devices
- Some features may require additional configuration
"This software has been a game-changer for our organization. Our endpoints are now more secure than ever before." - Happy Customer
Overall, I was highly impressed with the performance and effectiveness of this endpoint security software. It offers a wide range of features to keep your devices safe from various threats, and the user-friendly interface makes it easy to navigate and customize settings to fit your needs.
Key Features:
- Real-time threat protection
- Advanced endpoint security features
- Regular updates and patches
- User-friendly interface
FAQ:
Q: Is this software suitable for small businesses?
A: Yes, this software is a great choice for businesses of all sizes.
Q: Does it work on both Windows and Mac devices?
A: Yes, this software is compatible with both Windows and Mac operating systems.
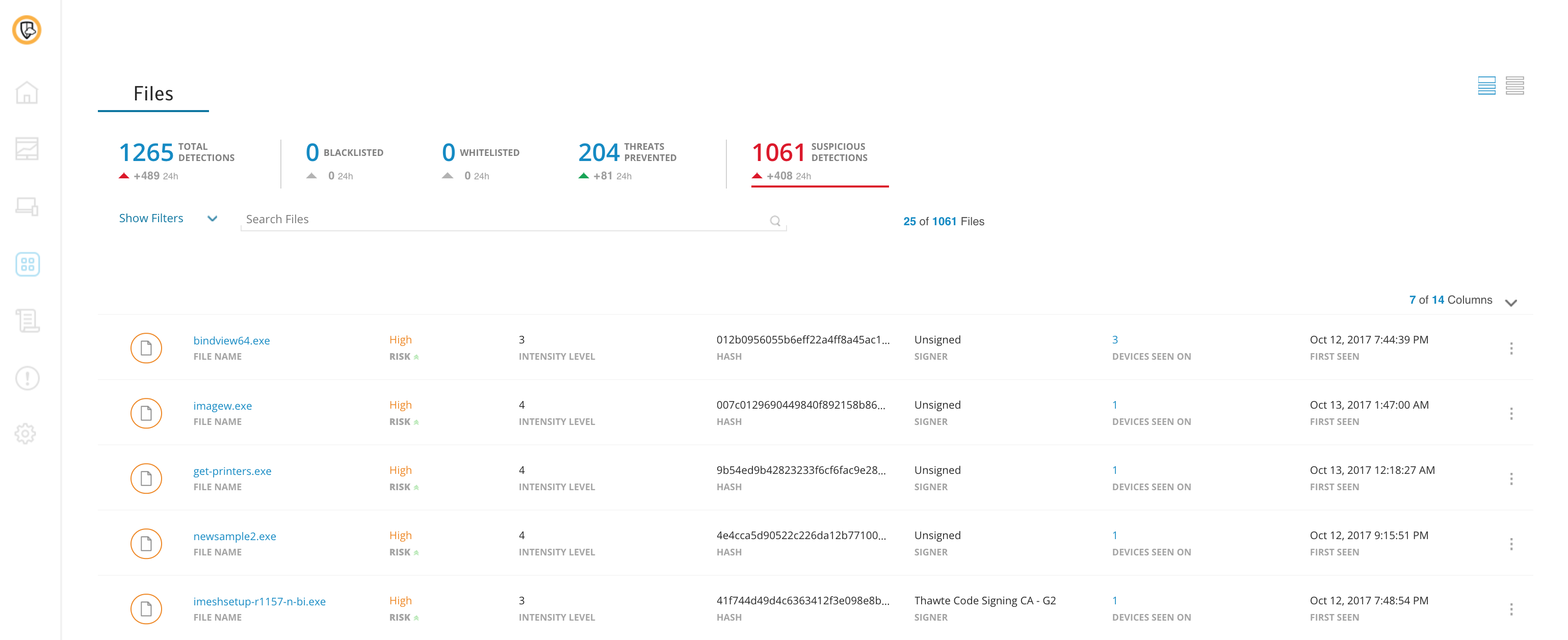
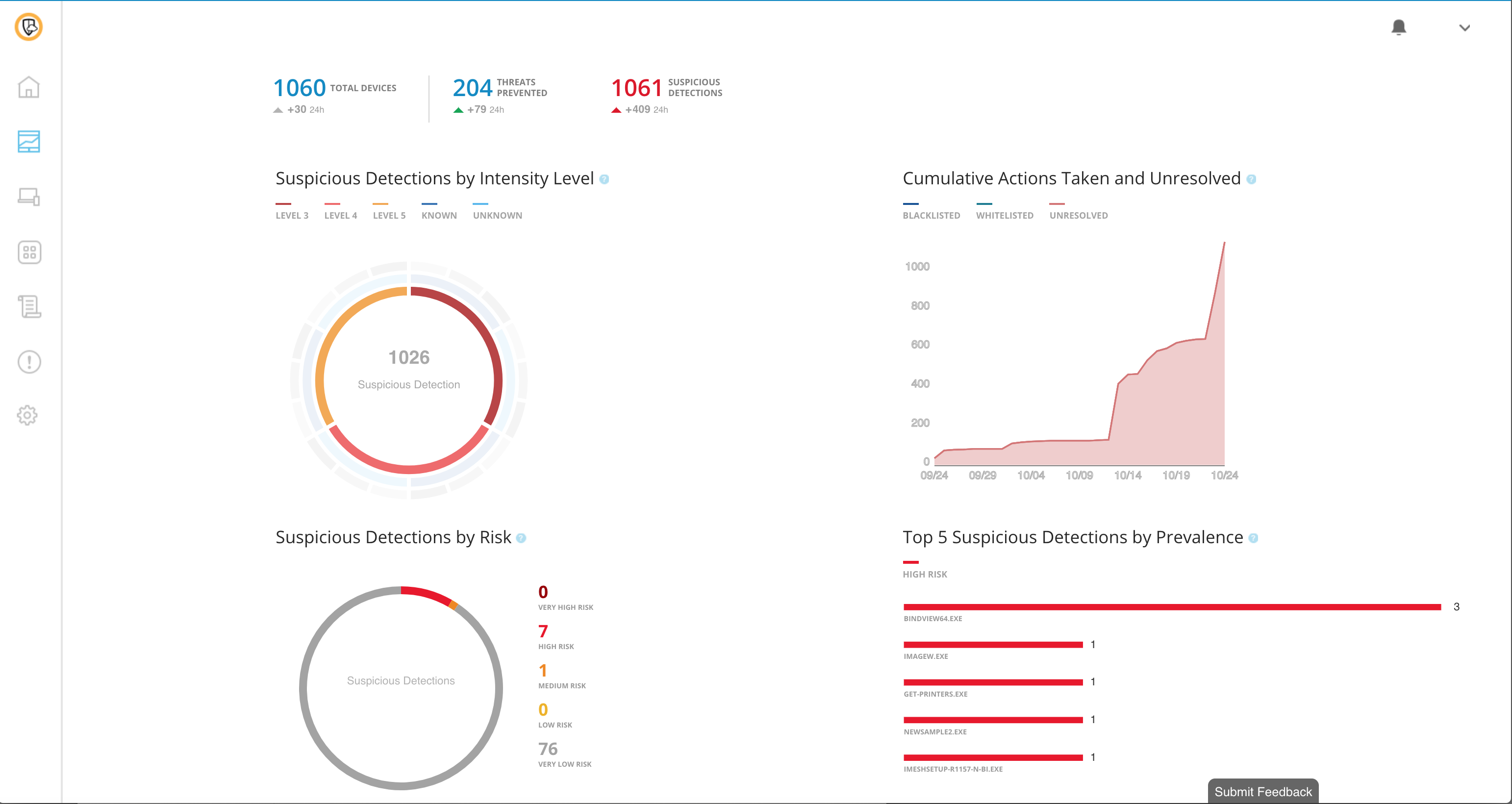
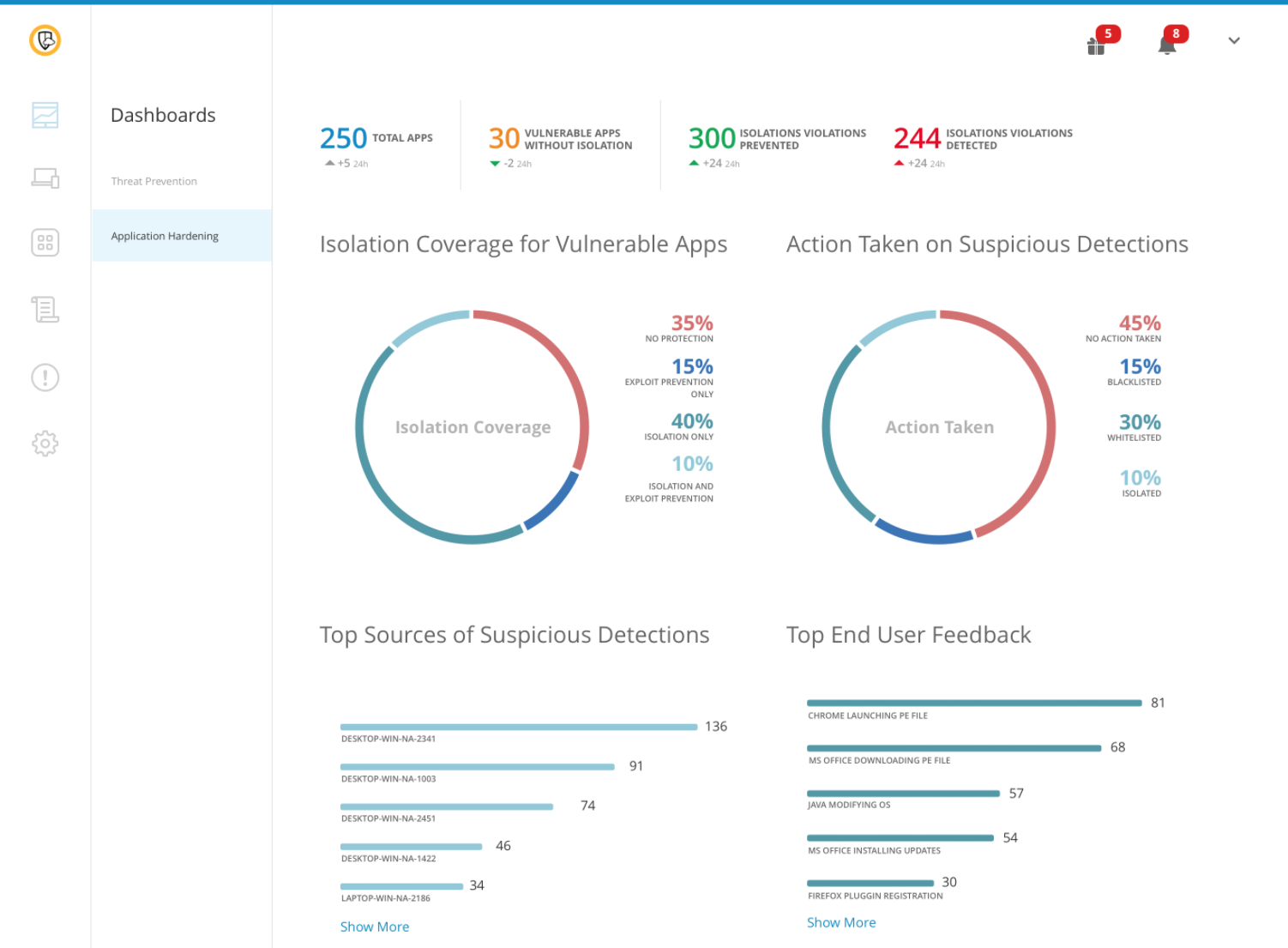
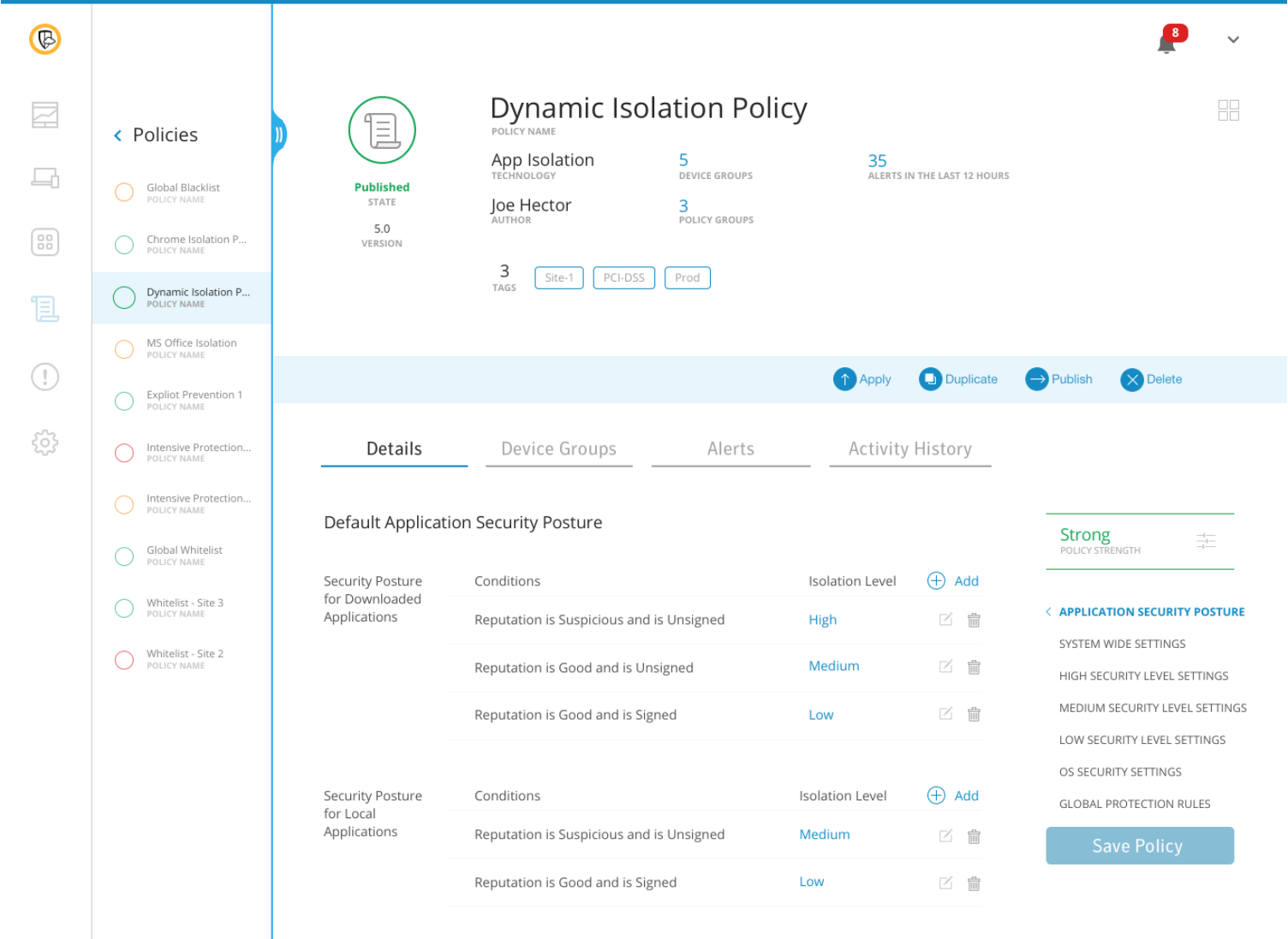
Overview of Symantec End-user Endpoint Security
Overview of Symantec End-user Endpoint Security Features
- Security audit reports
- Virtual environment protection
- USB device control
- Artificial Intelligence
- Intrusion prevention
- Central management console
- Data protection and backup
- Desktop firewall
- Content filtering
- Anti-spam
- Reputation-based spam filtering
- Device and app control
- Antivirus and spyware
- Advanced Machine learning














Add New Comment