GoodAccess Review
What is GoodAccess?
GoodAccess: Protect Your Network with Ease
As a technology enthusiast and avid user of various software solutions, I recently had the opportunity to test an impressive application that falls into the categories of Network Security Software, Virtual Private Network (VPN) Software, Zero Trust Networking Software, and Software-Defined Perimeter (SDP) Software. This powerful tool called GoodAccess truly exceeded my expectations and proved to be an indispensable asset in safeguarding my network and maintaining secure connections.
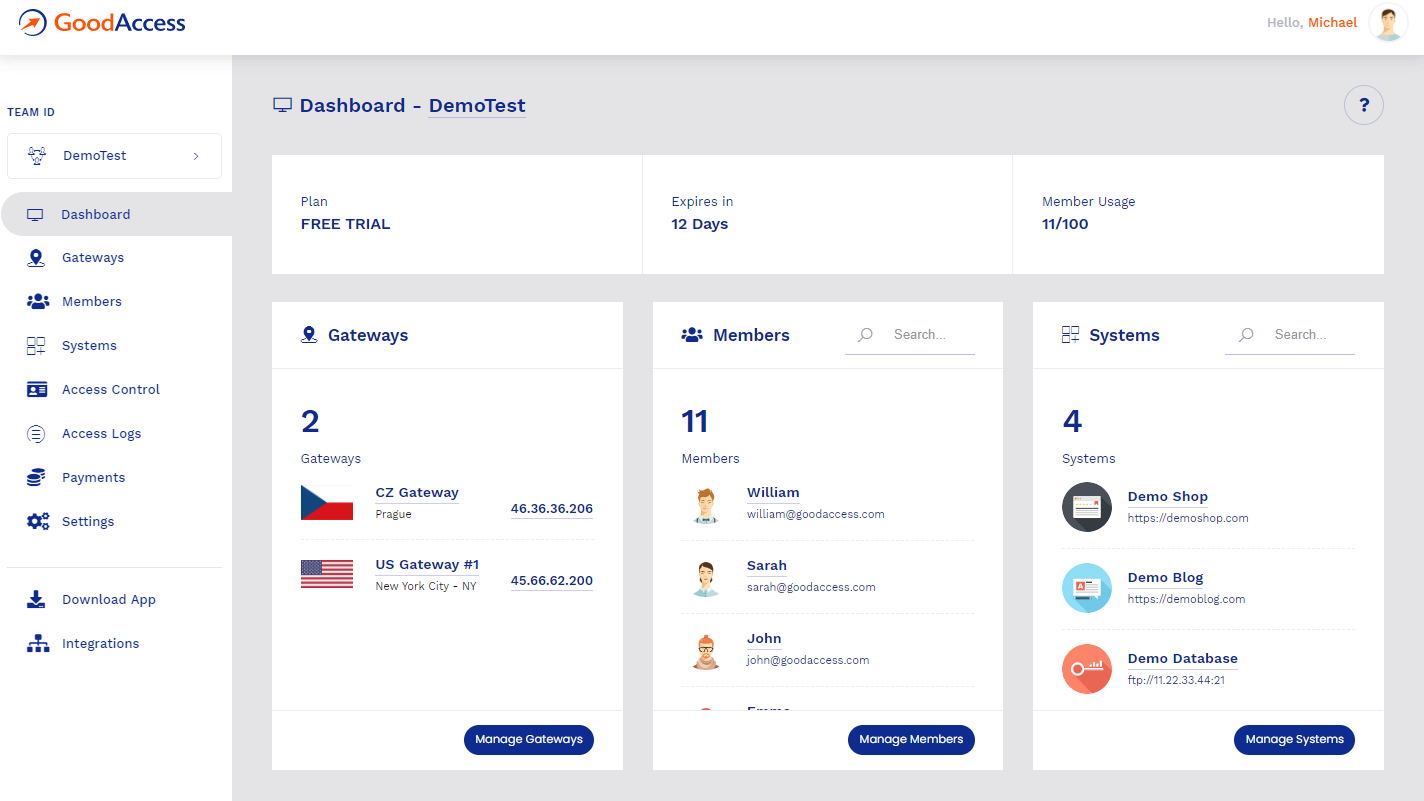
One of the standout features of GoodAccess is its user-friendly interface, which makes it incredibly easy to navigate and operate. Whether you are a seasoned IT professional or a novice user, the intuitive design ensures a smooth user experience and minimizes any learning curve that may be associated with it. With GoodAccess, you can start protecting your network and accessing secure connections in no time.
Unparalleled Network Security
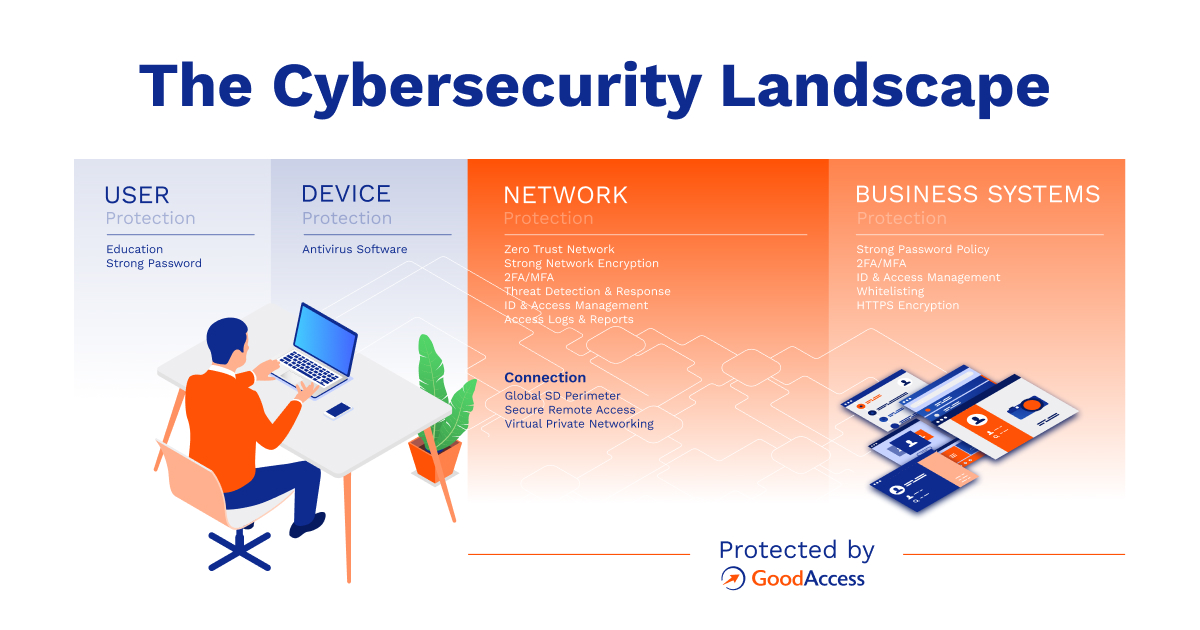
GoodAccess provides a comprehensive suite of network security features that are designed to keep your network safe from various threats, including hacking attempts, unauthorized access, and data breaches. This software employs a state-of-the-art encryption protocol, ensuring that your data remains secure and protected at all times. By leveraging cutting-edge technology, GoodAccess ensures that your network is fortified against even the most sophisticated cyber attacks.
Virtual Private Network (VPN) Capabilities
The virtual private network (VPN) capabilities of GoodAccess are truly remarkable. By establishing a secure connection between your device and the internet, this software enables you to browse the web, access corporate resources, and communicate with colleagues from any location, without compromising on security and privacy. The seamless integration and robust performance of GoodAccess VPN ensure a hassle-free and reliable internet experience.
Zero Trust Networking for Improved Security
GoodAccess adopts the Zero Trust Networking approach, which operates on the principle of never trusting a user or device by default, even if they are within the network perimeter. This innovative methodology significantly enhances network security by providing granular access control and continuously validating user identities. With GoodAccess, you can implement a strict Zero Trust Networking policy and mitigate the risk of internal and external threats.
Software-Defined Perimeter (SDP) Implementation
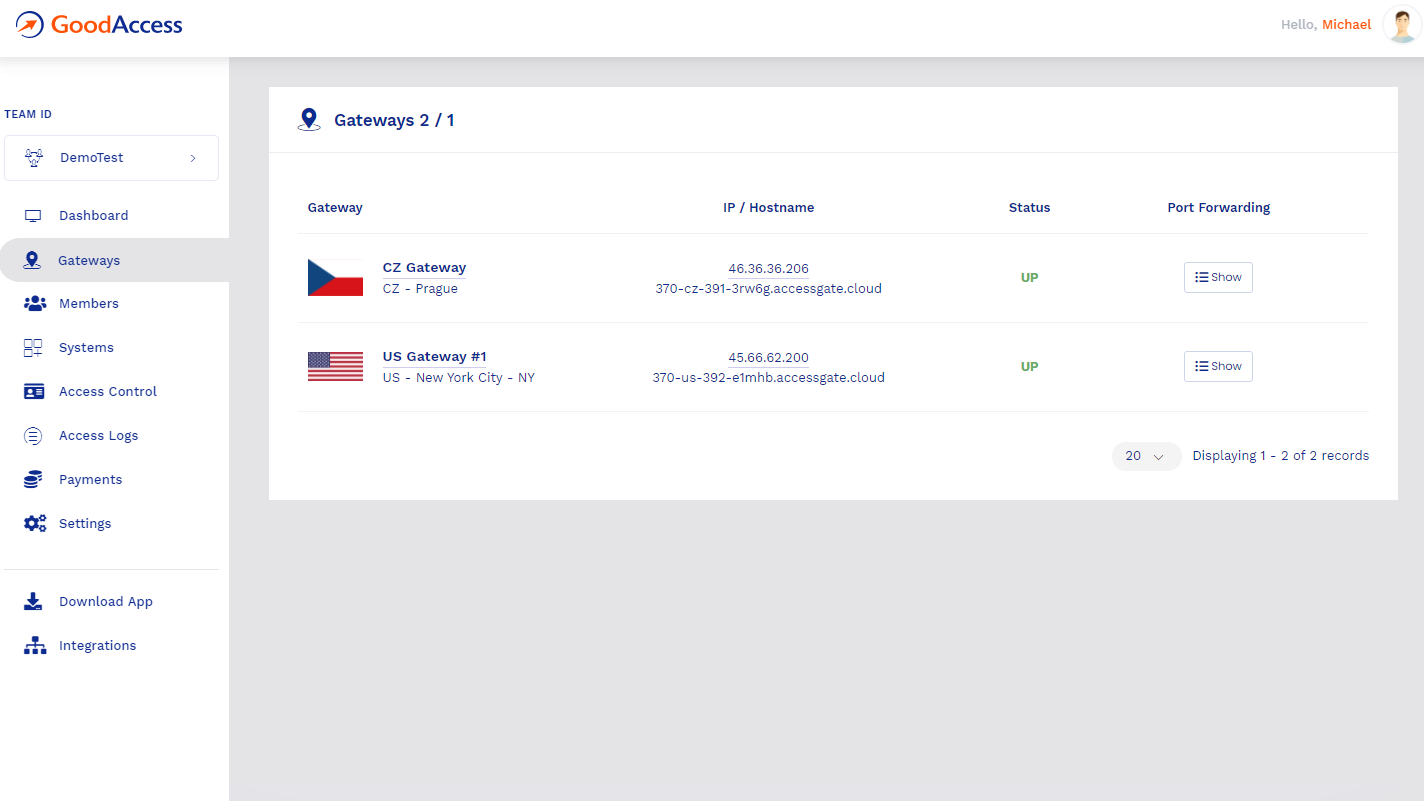
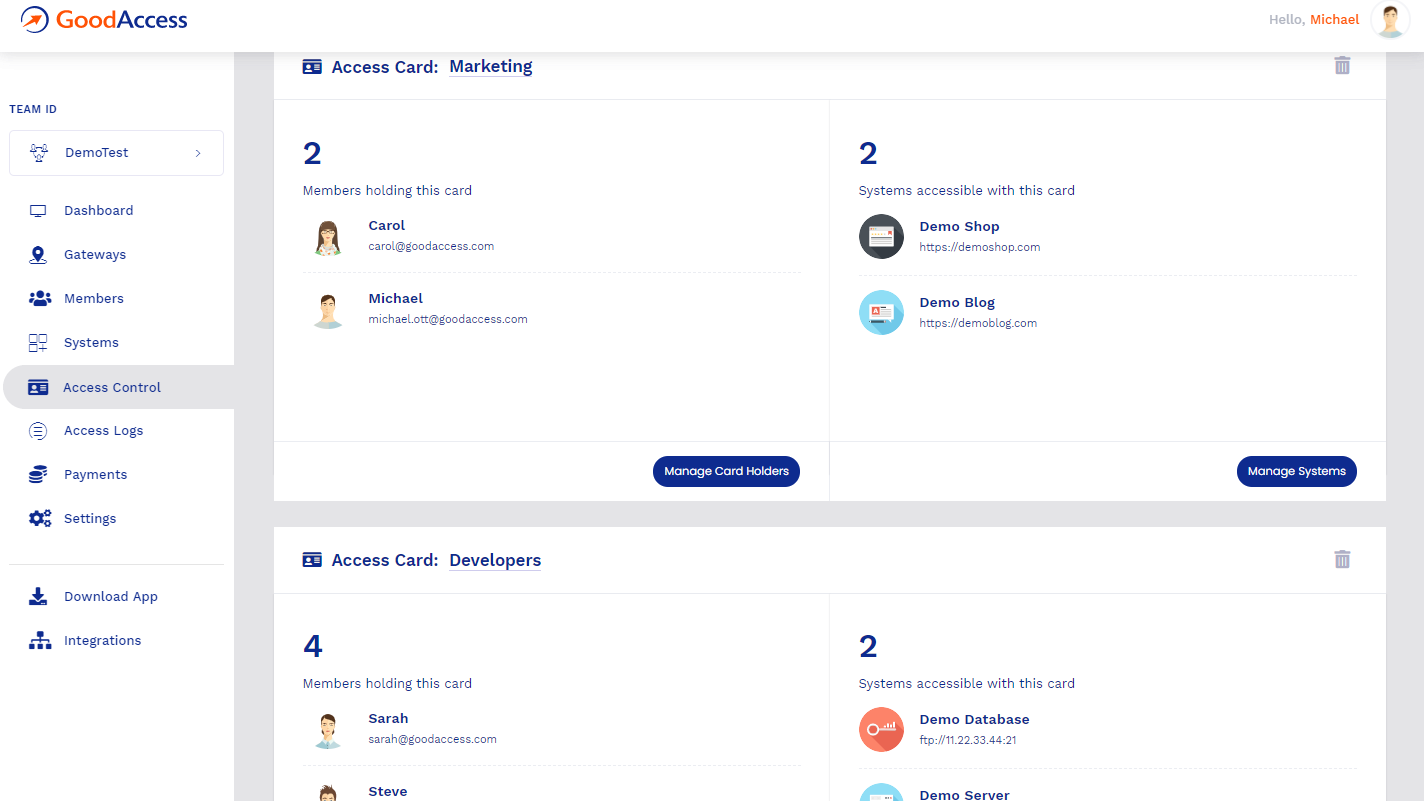
When it comes to implementing a Software-Defined Perimeter (SDP), GoodAccess stands out as an exceptional choice. This software effortlessly enables organizations to establish secure network connections, limiting access to only authorized users and devices. With GoodAccess's SDP capabilities, businesses can enjoy a higher level of network security, reduced attack surface, and increased control over access privileges.
Key Features of GoodAccess:
- Advanced network security measures
- Easy-to-use interface
- Virtual Private Network (VPN) functionality
- Zero Trust Networking implementation
- Software-Defined Perimeter (SDP) capabilities
Frequently Asked Questions (FAQ):
- What operating systems does GoodAccess support? GoodAccess supports a wide range of operating systems, including Windows, macOS, iOS, and Android.
- Is GoodAccess suitable for personal use? Absolutely! GoodAccess is an excellent choice for personal users who prioritize network security and secure internet browsing.
- Can GoodAccess be integrated with existing network infrastructure? Yes, GoodAccess is designed to seamlessly integrate with existing network infrastructure, ensuring a hassle-free implementation process.
- Does GoodAccess offer customer support? Yes, GoodAccess offers dedicated customer support to assist users with any inquiries or technical issues they may encounter.
















Add New Comment